Amazon.com: Data Blocker USB - USB Blocker,100% Guaranteed Prevent Hacker Attack.Any Other USB Device Charging,USB-Data Blocker.Data Blockers for Apple Products (5 Red) : Electronics

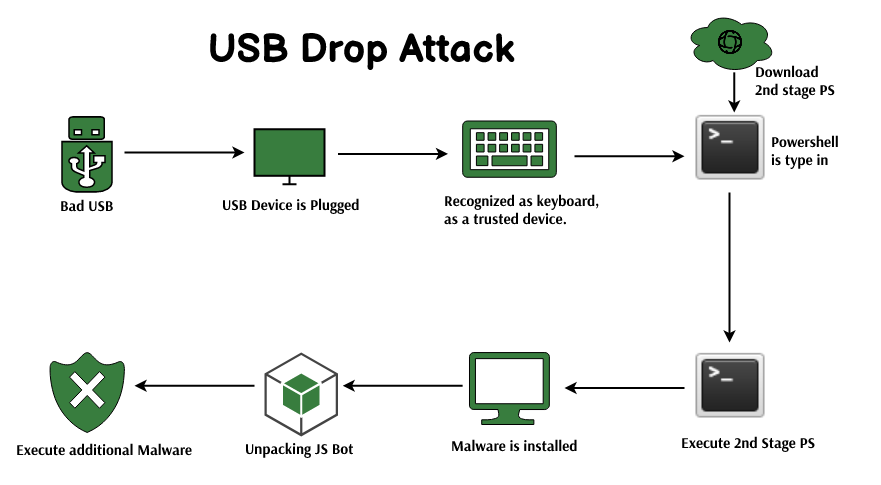
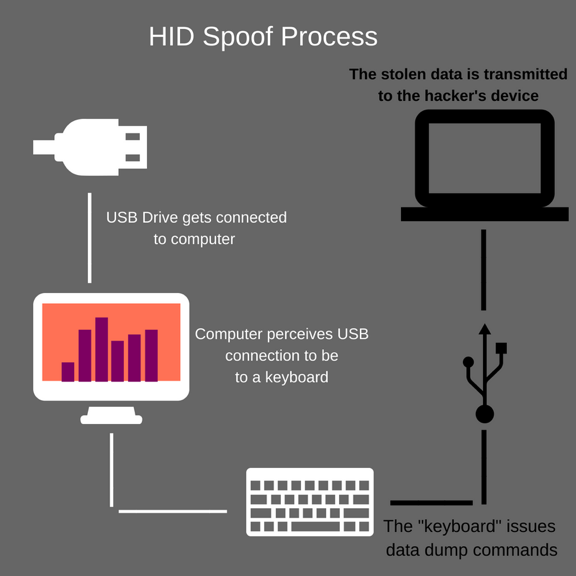
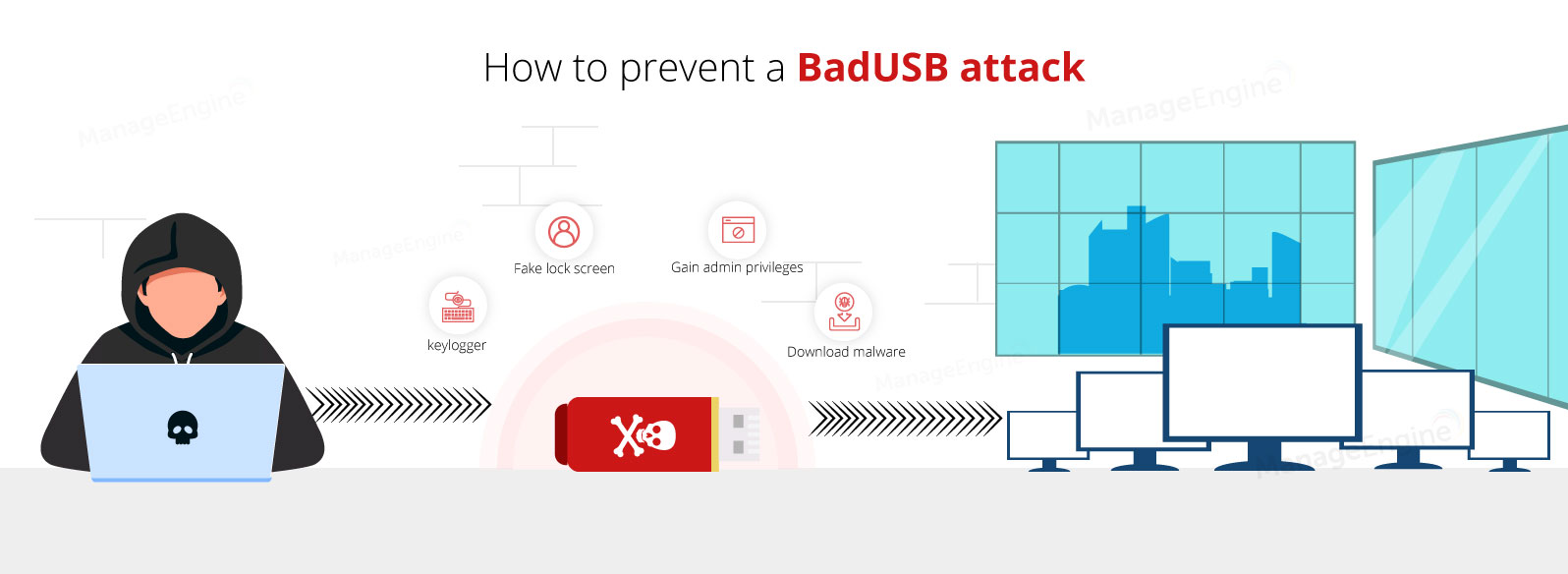
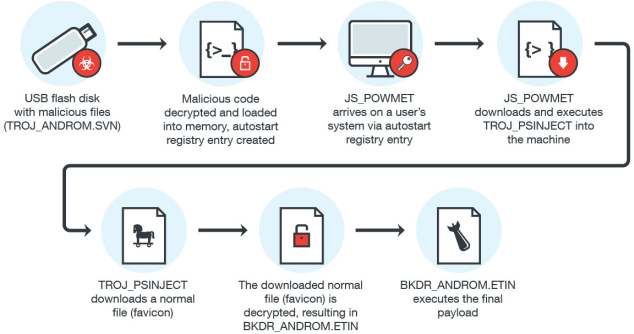
USB Continue to Threat Critical Infrastructure Security: 29 Ways to Attack Production Facility by USB